- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Collecting a packet capture from a Cisco IP Phone
Collecting a packet capture from a Cisco IP Phone
Introduction.
For troubleshooting purposes one may need to gather a packet (sniffer) capture from an IP Phone. There are many ways this can be accomplished. This article describes how to collect the capture using the IP Phone’s built in PC ports. It can be enabled to copy all traffic entering into the SWITCH port, and send it to the PC port. From there, the data can be captured using a packet capture utility.
These instructions are relevant for Cisco IP Phone Models, 7941, 7942, 7961, 7962, 7965, 7970, 7975, 99xx, 89xx, and 699xx.
For models 7940 and 7960, skip Step 2 since “Span to PC Port setting” is not required.
1. Connect the Cisco IP Phone
There should be a PC connected to the back of the IP phone in the PC port, and the phone connected to the Switch.
2. Enable the Span to PC port feature.
From the IP phone configuration page, scroll down to the Protocol Specific Configuration section, and enable the “Span to PC Port” configuration option. This will trigger a change to the phone’s TFTP configuration file. Save and reset the phone so it can retrieve the new configuration file.

![]()
| Note |
|---|
| 7940 and 7960 Cisco IP Phones do not support the span to PC port feature, all data is automatically sent to the PC port. |
3. Capture the packets with wireshark.
3a. Starting the capture
Open Wireshark and click on the first NIC to the left.
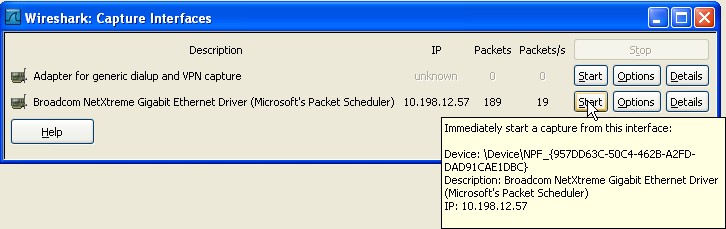
This will open the capture interfaces dialog, were you can select the NIC connected to the back of the IP phone we will capture. Click on start to initiate the capture
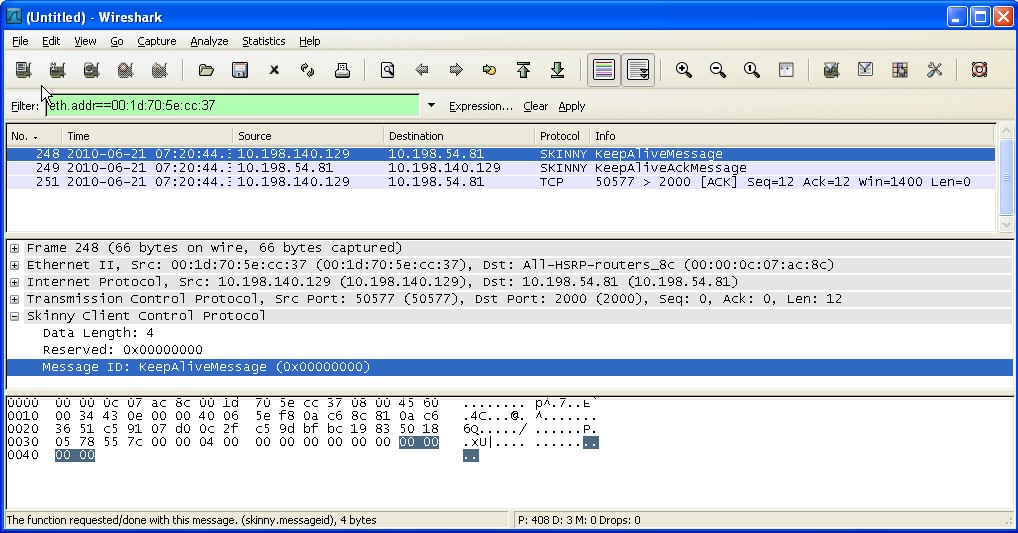
3b. Reproduce the issue to be captured
Traffic should start to scroll down on the window. Depending on the current PC activity it could be a lot of traffic. To filter down use the eth.addr filter with the MAC Address of the IP phone. The resulting traffic should show only traffic comming to and from the IP phone.
3c. Stop the capture.
3d. Save the packet capture as a .pcap file.